snootauth
can i tell you about this thing i wrote? it involves ssh and cookies and the setuid and setgid bits.
it’s called snootauth.
what is it?
it’s a way for sites on snootclub to verify a snootclub user.
how does it work?
it is hosted at /auth on any snoot site that wants auth.
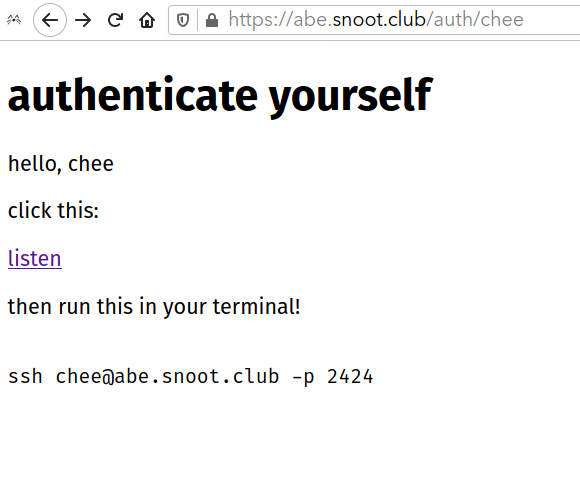
abe.snoot.club/auth/chee showing link labeled “listen”, and an ssh command to run
when you, a user, click the listen in the browser, it starts a GET request
which makes the server open a unix
socket that’s owned by your
user in /snoot/auth/socks/{your-uid}.sock.
there is an ssh
server running on
port 2424, which has ForceCommand set to a program called
succeed.
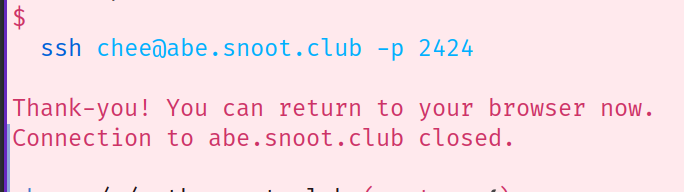
the ssh command being run in a terminal. “Thank-you, you can return to your browser now.”
when you run the ssh command, succeed(1) writes the word "success" to the socket belonging to your user then exits.
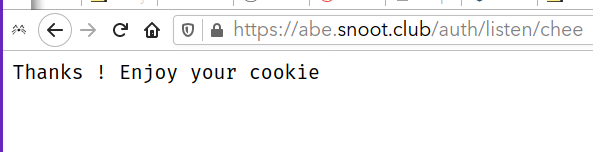
Web browser saying “Thank-you! Enjoy your cookie”
In the http server, listen’s GET request handler receives the "success" in the socket and returns, setting a cookie for you on the snoot subdomain you are on.
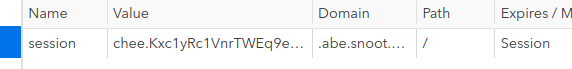
Devtools showing the cookie set for this subdomain.
and now on the server, there is a file that belongs to the snoot user whose site you are on that contains your token:
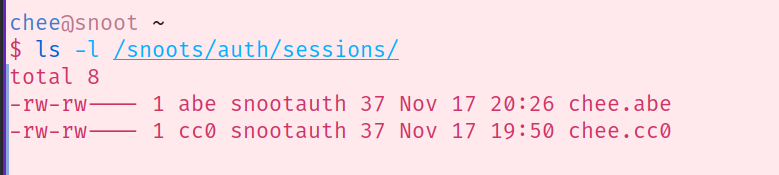
ls -l showing file permission abe:snootauth
it’s also read-writeable by the snootauth program, so it can delete or replace tokens when the user logs out or reauthenticates.
so now the server code for the snoot whose site you are on can check any cookies it receives against the token in /snoots/auth/sessions/{their-name}.{my-name} — chee (hi@chee.party) 2020-11-17